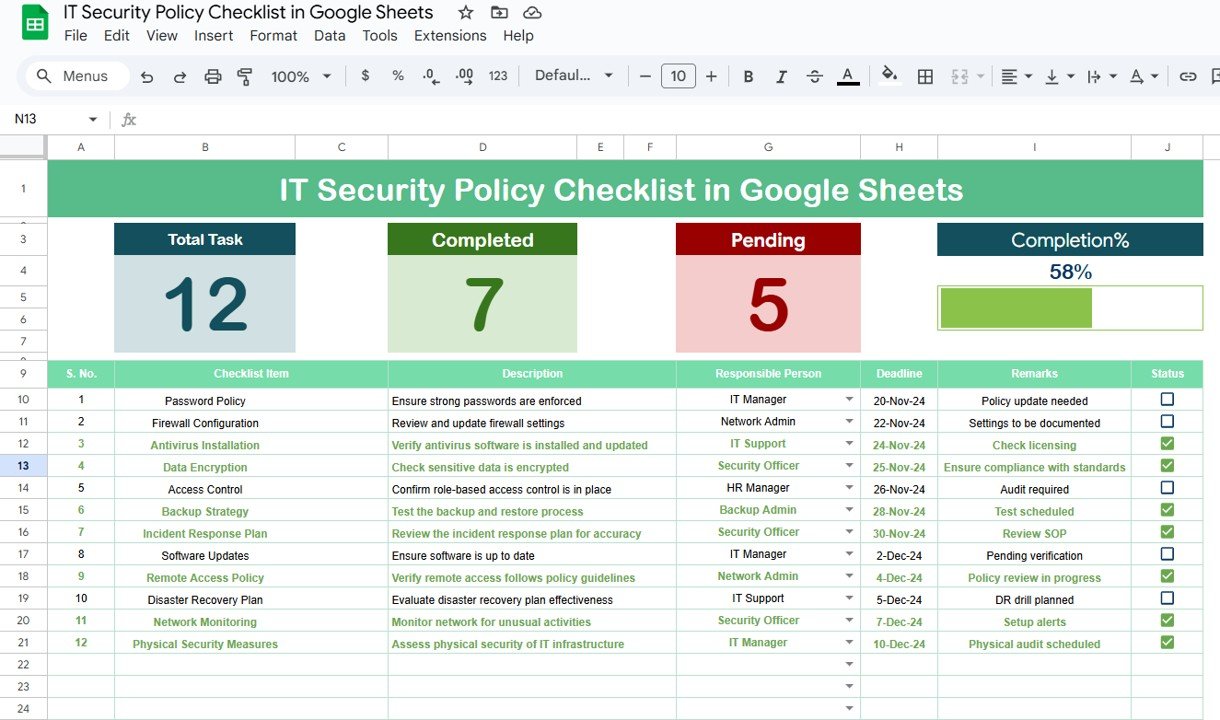
In today’s digital age, maintaining robust IT security is more critical than ever. With the growing complexity of cyber threats, businesses must ensure that their systems, networks, and data are secure. One effective way to keep track of security measures is by using an IT Security Policy Checklist. This article will explore how to use […]