In today’s digital age, maintaining robust IT security is more critical than ever. With the growing complexity of cyber threats, businesses must ensure that their systems, networks, and data are secure. One effective way to keep track of security measures is by using an IT Security Policy Checklist. This article will explore how to use an IT Security Policy Checklist in Google Sheets, highlighting its features, best practices, and the benefits it offers for enhancing your organization’s cybersecurity efforts.
Table of Contents
ToggleWhat is an IT Security Policy Checklist?
An IT Security Policy Checklist is a structured list of security-related tasks and actions designed to ensure that an organization follows best practices for safeguarding its information and technology systems. It serves as a guide for maintaining IT security protocols, such as data encryption, network monitoring, software updates, and employee training.
Using a checklist ensures that all necessary security measures are accounted for and tracked over time, which helps minimize security risks and comply with industry regulations.
Key Features of the IT Security Policy Checklist in Google Sheets
The IT Security Policy Checklist in Google Sheets is a ready-to-use template that simplifies the process of monitoring and maintaining your IT security policies. It is designed for easy tracking and efficient management. Below are the key features of this checklist template:
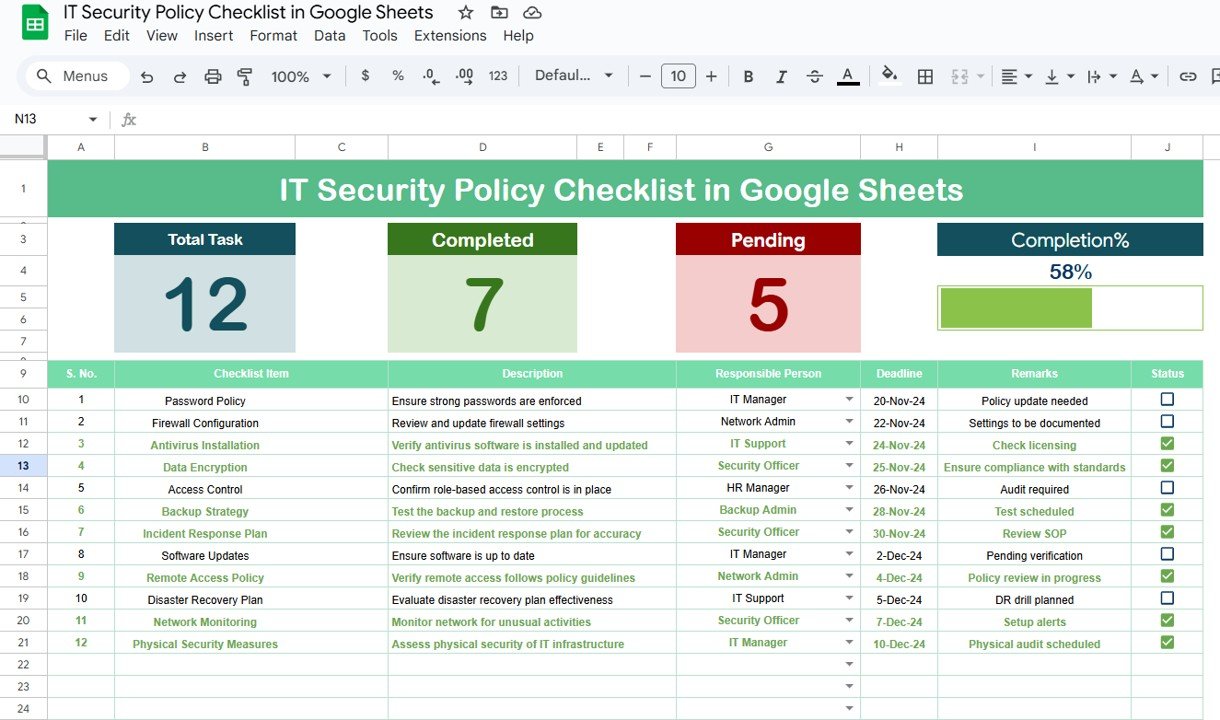
1. Main Checklist Sheet
The main sheet in the template is where all the checklist information is captured. This sheet is divided into sections that help you track and manage IT security tasks effectively.
Top Section: This section includes summary cards that display the total count of tasks, the number of completed tasks, the number of pending tasks, and a progress bar that shows the percentage of tasks completed. This provides a quick overview of your progress.
Checklist Table: This is the core of the template. It includes the following columns:
- Serial No.: A unique identifier for each checklist item.
- Checklist Item: The specific task or policy item related to IT security.
- Description: A brief explanation of the task or policy.
- Responsible Person: The person assigned to complete the task.
- Deadline: The deadline by which the task must be completed.
- Remarks: Any additional notes or instructions related to the task.
- Status: A column where the status of each task is tracked with a ✔ (completed) or ✘ (pending).
Click to buy IT Security Policy Checklist in Google Sheets
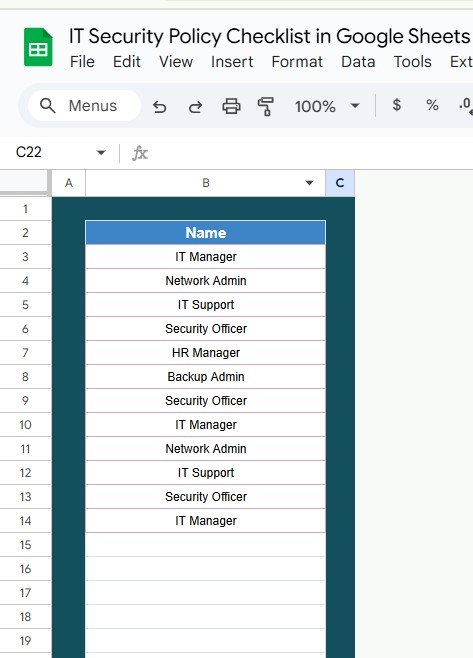
2. List Sheet Tab
The List Sheet tab is used to capture a unique list of responsible persons. This sheet is essential for creating a drop-down list in the main checklist table, making it easier to assign tasks and track progress. This ensures that only valid names are entered, streamlining the process of assigning responsibilities.
Advantages of Using the IT Security Policy Checklist in Google Sheets
Implementing the IT Security Policy Checklist in Google Sheets offers several advantages for organizations seeking to improve their IT security. Some of the key benefits include:
- Centralized Management: Google Sheets allows all your security tasks to be stored in one place, making it easier to manage and track them. You can access and update the checklist from anywhere, ensuring that all team members are on the same page.
- Real-time Collaboration: Google Sheets is a cloud-based platform, which means multiple users can collaborate in real-time. This feature allows IT teams and managers to work together, assign tasks, and monitor progress without the need for back-and-forth communication.
- Ease of Use: Google Sheets is user-friendly and does not require advanced technical skills. The template comes pre-built with all necessary columns and features, so you can start using it right away without spending time on setup.
- Trackable Progress: With built-in progress bars and task status tracking, you can easily monitor the completion of each security task. This helps identify bottlenecks and ensures that no critical security measures are overlooked.
- Customization: The template is fully customizable, meaning you can modify it to suit your specific IT security requirements. Whether you’re working with a small team or a large organization, you can tailor the checklist to fit your needs.
Opportunities for Improvement in the IT Security Policy Checklist
Click to buy IT Security Policy Checklist in Google Sheets
While the IT Security Policy Checklist in Google Sheets is a useful tool, there are always opportunities to enhance its functionality. Here are a few areas that could be improved:
- Automated Notifications: Google Sheets allows for automation through Google Apps Script. By setting up automated notifications, team members can be reminded when a task is nearing its deadline or if a task is overdue. This would help ensure timely completion of IT security tasks.
- Integration with Other Tools: For enhanced functionality, consider integrating the checklist with other project management tools or IT security software. This would allow for better synchronization of tasks and data, ensuring that all security-related activities are captured in one place.
- Advanced Reporting: The checklist could be expanded with advanced reporting features such as data visualizations, charts, and automated summary reports. These features could provide deeper insights into the status of security tasks and highlight areas where additional attention is needed.
- Task Dependencies: In larger organizations, certain IT security tasks might be dependent on the completion of others. Adding a task dependency feature would allow managers to better organize tasks and track progress more efficiently.
Best Practices for Using the IT Security Policy Checklist
To make the most out of your IT Security Policy Checklist, follow these best practices:
- Set Clear Responsibilities: Make sure each task is assigned to the right person. Use the Responsible Person column to assign tasks clearly, and ensure that each individual knows their responsibilities. This helps improve accountability and ensures that no tasks are overlooked.
- Regularly Update the Checklist: IT security is an ongoing process. Regularly update the checklist to reflect new policies, changes in responsibilities, or modifications to deadlines. Keep the checklist current to ensure that your security measures are always up to date.
- Monitor Progress Frequently: Track the progress of each task regularly. The Progress Bar and Status columns make it easy to see where tasks stand. By reviewing progress frequently, you can identify potential issues early and take corrective actions before problems escalate.
- Incorporate Feedback: As your team works through the checklist, encourage them to provide feedback on the process. Are there tasks that are too vague or difficult to complete? Are there ways to streamline the process? Use this feedback to improve the checklist and make it more effective.
- Review and Audit Periodically: Conduct regular audits of the IT security checklist to ensure that all tasks have been completed correctly. Periodically review the entire checklist to verify that all IT security measures are up to date and compliant with industry standards.
Frequently Asked Questions (FAQs)
Click to buy IT Security Policy Checklist in Google Sheets
1. What is an IT Security Policy Checklist?
An IT Security Policy Checklist is a list of security tasks and measures that organizations use to ensure the safety of their systems and data. It helps track tasks such as software updates, network monitoring, data encryption, and employee training.
2. How does the IT Security Policy Checklist in Google Sheets work?
The checklist is a pre-configured template that tracks IT security tasks. It includes columns for checklist items, descriptions, responsible persons, deadlines, and task status. You can use Google Sheets to update and manage the checklist in real-time.
3. Can I customize the IT Security Policy Checklist?
Yes, the checklist is fully customizable. You can add or remove columns, modify the task descriptions, and tailor the template to fit your organization’s specific IT security needs.
4. How can I automate reminders for deadlines in Google Sheets?
You can use Google Apps Script to set up automated reminders for upcoming deadlines or overdue tasks. This feature will send notifications to responsible persons to ensure timely completion of tasks.
5. Can I use the IT Security Policy Checklist for other purposes?
While the template is designed for IT security, it can be customized for other purposes as well. You can adapt it for any checklist-based task management system in your organization.
Conclusion
Click to buy IT Security Policy Checklist in Google Sheets
The IT Security Policy Checklist in Google Sheets is an essential tool for any organization looking to improve its IT security posture. It helps ensure that all necessary security measures are tracked, assigned, and completed on time. With its user-friendly design, customizable features, and real-time collaboration capabilities, this checklist template makes it easier to maintain robust IT security policies and safeguard your organization’s digital assets. By following best practices and leveraging opportunities for improvement, your team can effectively manage and enhance your IT security policies, ensuring a secure and compliant digital environment
Visit our YouTube channel to learn step-by-step video tutorials
Youtube.com/@NeotechNavigators